Cybersecurity is becoming an increasingly urgent concern for process manufacturing companies. Virus scanners, firewalls and passwords alone no longer offer sufficient protection against hackers. What they need is a comprehensive security solution tailored to their unique situation.
The production and automation levels of process manufacturing plants are increasingly interconnected, both with each other and with the Internet. The advantages of connectivity, however, are accompanied by heightened susceptibility to sabotage and tampering through malicious software like viruses, trojans and worms. As these threats continue to grow, companies are on the search for the best way to protect their systems.
At the 2016 Hannover Messe trade fair, Germany's digital industry association, Bitkom, revealed just how high the risks already are. A survey of 504 manufacturing companies conducted by the association showed that 69% had fallen victim to data theft, industrial espionage or sabotage in the past two years. Accounting for more than a third of the incidents, the most common offense was the theft of smartphones, computers or tablets. A further 18% reported acts of sabotage aimed at disrupting or crippling business operations.
Planning and risk assessment
Virus scanners, firewalls and passwords are already standard components of any IT security solution. "To protect a process control system from cyber attacks, however, these measures alone are not enough," says Martin Reichinger, manager of B&R's process automation business unit. According to Reichinger, the design process for any new processing plant should include a risk assessment that can be used to develop a comprehensive plan for cybersecurity. After all, the right security strategy depends on the processes, infrastructure and other local conditions. "There is no one-size-fits-all solution when it comes to cybersecurity," emphasizes Reichinger.
Security cells for maximum availability
One component of a security concept might be to isolate processing steps into task-specific cybersecurity cells. This helps ensure the availability of the system as a whole, as Reichinger explains: "In the event that certain infrastructure elements are affected by an attack, the other cells are able to continue operation. A threat within any one cell is restricted to that cell alone."
If a process is unsuitable for division into cells – due to a lack of buffer containers, for example – the system can alternatively be safeguarded by assigning task-specific user rights for access and operation. "What's important is that you define these areas of responsibility under consideration of all production levels," says Reichinger. As a fundamental principle, access permissions should only be established where they are absolutely necessary.
Dual firewalls for double protection
"There are numerous methods for protecting process control systems from cyber attacks," says Reichinger. Tamper resistance is always an important feature. The security architecture must be designed to provide maximum protection against manipulation of important data.
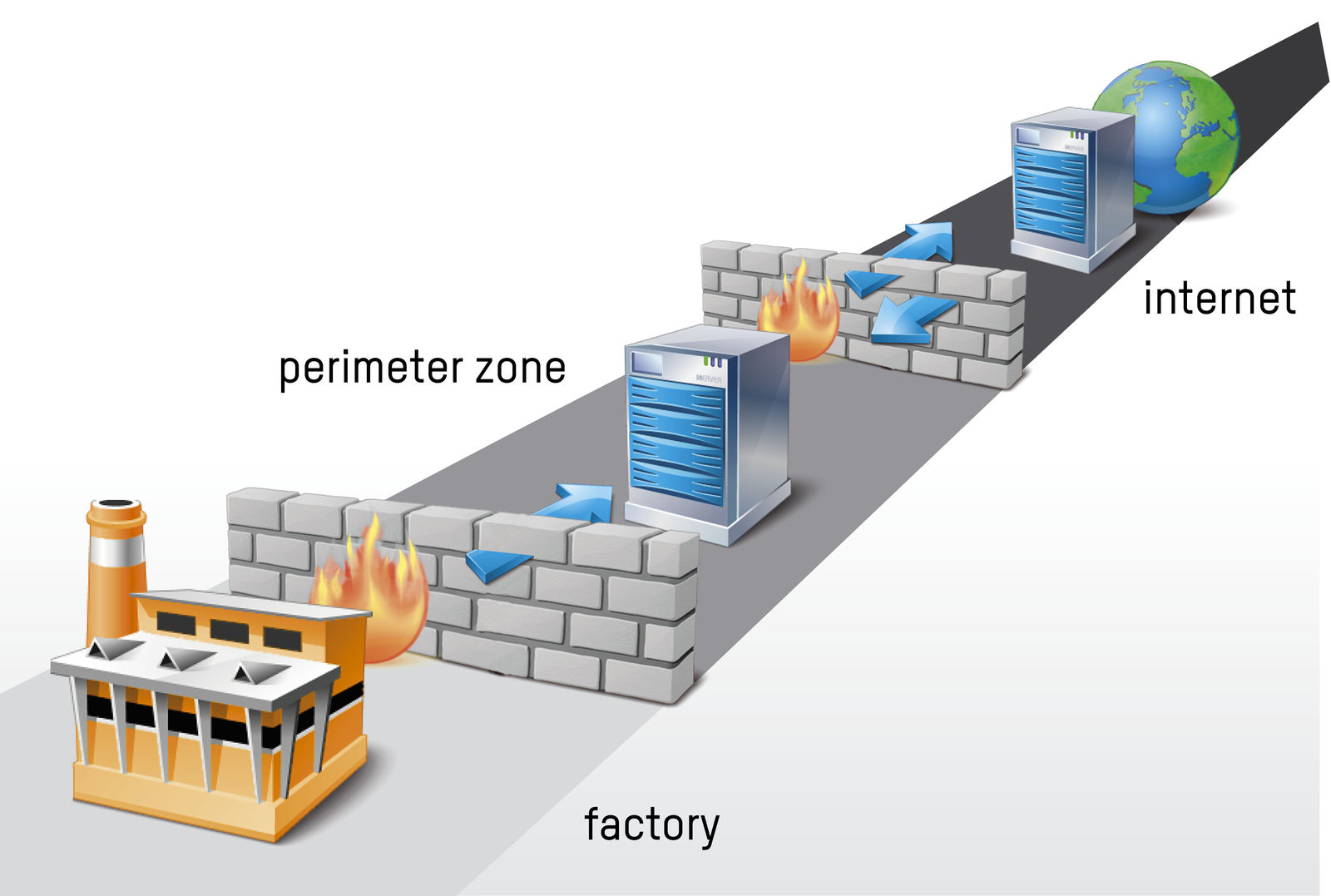
The foremost rule for process control systems is that they are isolated from higher-level systems by a secure perimeter network, known as a demilitarized zone or DMZ. Data from the process control system is first transferred to this perimeter network before it can be accessed from the outside. The perimeter network is guarded by either a triple-homed firewall, which enables it to be connected separately, or two firewalls from different manufacturers. "In most cases, this solution provides sufficient time to detect and block an attack in the event that the first firewall is breached," says Reichinger. Deep packet inspection technologies are also used to detect unauthorized operations in real time.
SQL databases particularly secure
Among APROL's most significant benefits, according to Reichinger, is that its SQL server grants external networks exclusively read-only access. This severely hampers the ability of hackers to manipulate data on the servers from the outset. Additionally, all APROL servers are equipped with an integrated firewall. "The firewall is installed and configured automatically at the first startup," says Reichinger. To offer the best possible security, APROL is based on the operating system SUSE Linux Enterprise Server 12 SP4.
Minimizing points of attack
Germany's Federal Office for Information Security (BSI) stipulates that system software be hardened – a requirement that B&R satisfies with APROL 4.0 and higher. These versions contain only software components and functions that are essential to the program's ability to fulfill its intended task. Often, attackers are able to gain access to a server by misusing a program that never needed to be there in the first place. "Similarly, it is also important to close up unused ports and hardware interfaces that would otherwise allow someone to insert a flash drive and upload malicious software," notes Reichinger.
He concludes with one final consideration: "Not even the best security design can protect you against everyday carelessness." Particularly serious risks are posed by weak passwords, poorly maintained user permissions and failure to keep software up to date. "Security must be a top priority for plant operators over the entire lifespan of the system."
Safety and security
Safety and security are two critically important aspects of industrial manufacturing. Safety technology prevents humans from being harmed by the equipment they are operating. Before an accident is able to occur, the safety technology must guarantee that the machine or line shuts off automatically or slows down sufficiently to eliminate the risk. Security technology, on the other hand, prevents systems from being intentionally manipulated by humans. In the field of IT, security threats include trojans, viruses and hacker attacks. As humans and machinery operate more and more closely together, both safety and security are taking on increasing significance.

Martin Reichinger, Business Manager - Process Automation, B&R